EC-Council Key Takeaways:
- Information security means protecting information from unauthorized access and threats and ensuring its confidentiality, integrity and availability.
-
The role of IT security is critical to protecting an organization's information assets and technologies. It encompasses a range of practices to secure computers, networks and data from cyber threats.
-
IT security refers to the strategies and measures used to protect IT assets against cyber threats, including network security, application security and more.
-
EC-Council certifications are designed for IT professionals who specialize in IT security. Certifications, such as EC-Council Certified Ethical Hacker (CEH), EC-Council Certified Cybersecurity Technician (CCT) and Certified Security Analyst (ECSA), validate expertise in various areas of cybersecurity and prepare individuals for specialized roles in these areas.
-
EC-Council certifications are critical to validate IT security skills and prepare for careers in cybersecurity. There are a variety of programs in different security fields for this purpose.
-
In this introduction, you will learn more about EC-Council training and find an overview of the available training courses. For the next step, you can register here for the EC-Council training course of your choice.
Introduction to EC-Council Training
What is EC Council Training
EC-Council's certification programs validate required expertise and skills in the field of IT security. EC-Council offers training modules for any individual interested in learning more about the topic of information security and its various areas. From the basics of network security to some fundamental security domains, our experienced trainers will help you understand these topics more easily.
EC-Council certifications give you a competitive edge in your career. For example, they position you as an ethical hacker, digital forensics investigator and encryption specialist.

What is an EC-Council training for?
The EC-Council Certified Ethical Hacker, Certified Incident Handler, Licensed Penetration Tester, Certified Forensic Investigator etc. are some of the highly advanced online hacking courses in the field of information security offered in the United Kingdom (UK). Cyber Security Training courses are specifically designed to impart skills and knowledge to individuals who are interested in working towards maintaining and protecting an organization's mainframe from malicious cyber attacks and cyber threats.
EC-Council offers many different certifications. We have listed the most popular ones for you here.
EC-Council Certification Programs
1. EC-Council Certified Chief Information Security Officer (CCISO)
The Certified Chief Information Security Officer (CCISO) certification is a highly specialized certification that focuses on preparing information security executives for top leadership positions. In addition to providing information security leadership, CCISOs also perform risk management and project management functions. Upon completion of the course, participants will have advanced technical skills in cybersecurity and risk management and will be able to effectively manage an organization's security.
To sit for the CCISO exam and receive certification, participants must meet the basic CCISO requirements. Candidates who do not yet meet the CCISO requirements but are interested in information security management can pursue the EC-Council Certification: Information Security Management (EISM).
What are the five CCISO domains?
The five CCISO domains are:
- Governance, Risk, Compliance
- Information security controls and audit management
- Management and operation of security programs
- Core competencies in information security
- Strategic planning, finance, procurement and third-party funding management
Exam information
To obtain the EC-Council Certification, CCISO, each applicant must pass the exam, which covers all 5 CCISO domains, regardless of experience in each domain. The exam consists of 150 multiple-choice questions administered over a two and a half hour period. The questions on the exam require extensive thought and evaluation.
There are three cognitive levels tested on the CCISO exam
- Level 1: Knowledge: This cognitive level of questions is used to recall memorized facts.
- Level 2: Application: This cognitive level of questions is used to test the candidate's ability to apply and understand specific concepts.
- Level 3: Analysis: This cognitive level of questions is used to test the candidate's ability to identify and solve a problem given a range of variables in the appropriate context.
How long is the CCISO certification valid for?
The C|CISO certification is valid for a period of three years.
What do I have to do to renew my certification?
To renew your certification, you must fulfill the continuing education requirements.
Information Security Manager (EISM) Program
The EISM program allows participants who are not yet qualified for the CCISO exam to complete the training course and obtain an EC-Council certification. EISM participants can apply for the CCISO exam once they have gained the relevant experience.
Information Security Manager (EISM) program
The EISM program allows participants who are not yet qualified to take the CCISO exam to complete the training course and earn an EC-Council certification. EISM participants can apply for the CCISO exam once they have gained years of experience.
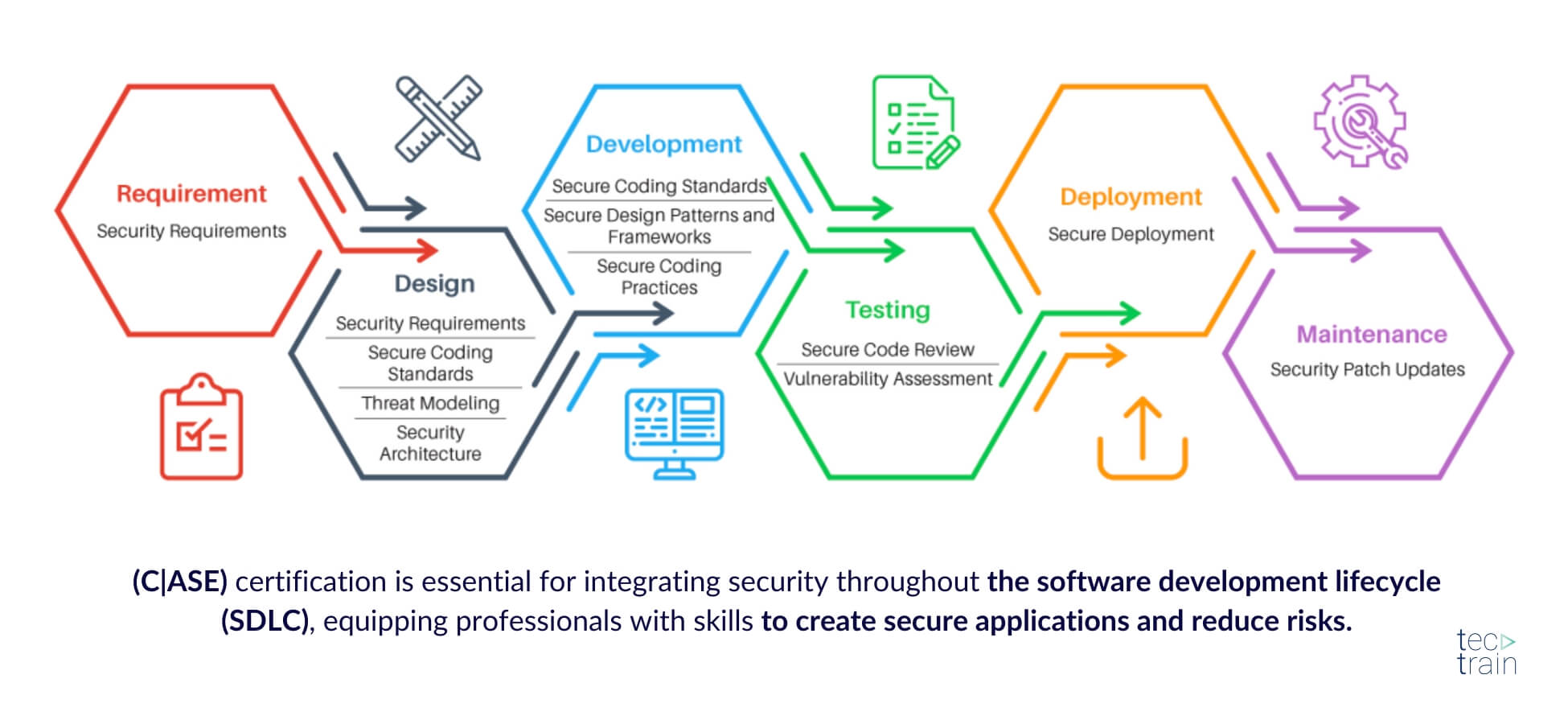
2. EC-Council Certified Application Security Engineer (.NET & Java)
Certified Application Security Engineer (CASE . NET)
The Certified Application Security Engineer (CASE) certification was developed in collaboration with major application and software development experts worldwide.
The purpose of CASE is
- To ensure that application security is no longer in the background, but in the foreground.
- To create a foundation that can be used by all application developers and development organizations to build secure applications with greater stability and lower security risks to the consumer and make security a primary consideration.
- To minimize the risk of companies losing millions due to security threats that can occur at every step of the application development process.
- To help individuals develop habits to give more importance to security, thus opening up security as the main domain for testers, developers, network administrators, etc.
Why become a Certified Application Security Engineer?
- Instant credibility: The CASE program confirms that you are indeed an application security expert. It demonstrates your skills that could be relevant to employers worldwide.
- Relevant knowledge: You can expand your application security knowledge through the EC-Council CASE certification.
- Versatile skills: CASE can be applied to a variety of platforms, including mobile apps, web apps, IoT devices and many more.
- A holistic view: CASE spans from pre-deployment security techniques to post-deployment security techniques, covering every aspect of the secure software development lifecycle and equipping you with the skills necessary to build a secure application.
Eligibility Criteria
To be eligible to apply for the CASE exam, a participant must fulfill at least one of the following criteria:
- Attend official EC-Council CASE training by an accredited EC-Council partner
- Be an ECSP (.NET/ Java) member in good standing
- Have at least 2 years of work experience in InfoSec / Software field
- Have other industry-standard certifications such as GSSP .NET/Java
Who is the EC-Council Certified Application Security Engineer certificate suitable for?
-
.NET developers with at least 2 years of experience and people who want to become application security engineers, analysts or testers.
-
Individuals involved in the development, management testing or protection of a broad range of applications.
Certified Application Security Engineer (CASE Java)
The CASE certified training program is concurrently developed to prepare software professionals with the necessary skills expected by employers and universities worldwide. It is designed as a hands-on, comprehensive application security course that helps software professionals create secure applications.
The training program covers security activities involved in all phases of the Software Development Lifecycle (SDLC): Planning, building, testing and deploying an application. Unlike other application security training, CASE as an EC-Council certification goes beyond the guidelines for secure coding practices and includes secure requirements gathering, robust application design and addressing security issues in post-development phases of application development. This makes CASE one of the most comprehensive EC-Council certifications on the market today.
Microdegree in Python Security
The Python programming language is one of the most popular languages currently in use. Not only is it easy to learn and use, but it also offers great support for a range of fields, from data science to cybersecurity. In this microdegree, you will explore the different possibilities and aspects that Python is used for, which in turn can help you start or advance your career in any technology field of your choice.
What are the prerequisites for joining the program?
Basic working experience with Python is expected.
Microdegree in PHP Security
This course is aimed at PHP professionals who want to increase their awareness and knowledge of security principles. It will help you write better code, recognize common issues and use tools that identify problems. If you want to progress in your PHP career by building your skills, then this course is for you!
What are the requirements to join the program?
Ideally, you should have at least one year of experience in PHP. However, to get the most out of this course, all you need is a desire and willingness to learn.
Python Programming for Beginners: Designed for beginners with little to no understanding of programming, this course will give you the knowledge to start programming with Python 3.
The following topics are covered in this course:
- Python installation
- Running Python scripts in the terminal
- PyCharm IDE setup
- Numbers, strings, boolean operators, lists, dictionaries and variables
- Functions, arguments, return values, loops and modules
Who this course is for:
This course is just right for newcomers to programming or the Python language, as well as computer security professionals and network administrators interested in programming and developing security applications.
Web Application Hacking and Security
Web Application Hacking and Security is a specialization certification that enables you to hack, test and protect web applications from existing and emerging security threats in the industry. Web Application Hacking and Security is the only experiential program that provides comprehensive knowledge and 100% hands-on learning. It helps cybersecurity professionals protect web applications from existing and emerging security threats and test hacking. Test your skills and learn to excel in web application security testing. Whether you're a beginner or an experienced ethical hacker, the Web Application Hacking and Security course has something for everyone.
Who should attend the course?
If you are tasked with implementing, managing or protecting web applications, this course is for you. Also, if you are a cyber or tech professional interested in learning mitigation methods for a variety of web security issues and want a pure hands-on program, then this is the course you've been waiting for.
3. EC-Council Certified Cybersecurity Technician (C|CT)
This EC-Council certification enhances employability by validating certification holders' skills as cybersecurity specialists who can strengthen organizational security. It also provides extensive opportunities to practice the practical skills required for any technical role with administrative rights and cybersecurity considerations.
The EC-Council Certification C|CT program enables individuals to expand their skills in a variety of roles, including penetration testing, security consulting, auditor and administrator roles and beyond. It builds a foundation of technical skills required to create successful technologists necessary in various job roles.
Job opportunities and job roles for C|CT credentialing
The EC-Council Certified Cybersecurity Technician credential prepares IT and cybersecurity professionals to tackle a variety of complex problems focused on securing software, networks and IT systems while understanding common threats and attacks. C|CT provides a multi-faceted approach to network defense, ethical hacking, and security operations to ensure that individuals use their strongest skills to configure, analyze, and identify problems in their organization.
This course prepares and enhances skills in the following roles:
- IT Support Specialist
- IT Network Specialist
- Cybersecurity Technician
- Network Engineer
- SOC Analyst
- IT manager
4. EC-Council Computer Hacking Forensic Investigator (C|HFI)
This program is designed for IT professionals involved in information systems security, computer forensics and incident response. It will help strengthen the application knowledge in digital forensics for forensic analysts, cybercrime investigators, cyber defense forensic analysts, incident responders, IT auditors, malware analysts, security consultants and chief security officers.
The program equips participants with the necessary skills to proactively address complex security threats and investigate, record and report cybercrime to prevent future attacks.
EC-Council's Certified Hacking Forensic Investigator (CHFI) is the only comprehensive ANSI-accredited, lab-based program on the market that provides organizations with vendor-neutral training in digital forensics. The EC-Council Certification in CHFI provides its participants with a solid understanding of digital forensics and presents a detailed and methodical approach to digital forensics and evidence analysis that also focuses on dark web, IoT and cloud forensics. The tools and techniques covered in this program prepare the learner to conduct digital investigations using groundbreaking digital forensics technologies.
Careers with CHFI
Certified Hacking Forensic Investigator v10 has been developed by industry experts to provide an unbiased approach to the application of complex investigative practices and empower forensic professionals:
- To take an active role in the investigation and preservation of digital and non-digital evidence of an attack.
- Act against a range of compromises.
- Use threat intelligence to anticipate and alert cyber teams in the event of future attacks.
Who is the EC-Council certification CHFI suitable for?
The EC-Council Computer Hacking Forensic Investigator (C|HFI) certification is aimed at all IT professionals involved in information systems security, computer forensics and incident response.
Target group
- Police and other law enforcement personnel
- Defense and security personnel
- E-business security experts
- lawyers
- Banking, insurance and other professionals
- Government authorities
- IT managers
- Service provider for digital forensics
5. EC-Council Certified Ethical Hacker (C|EH)
The EC-Council Certified Ethical Hacker program focuses on hacking techniques and technologies from an offensive perspective. This advanced security program is regularly updated to reflect the latest industry developments, including new hacking techniques, exploits, automated programs and defensive recommendations outlined by experts in the field. The CEH body of knowledge represents detailed contributions from security experts, academics, industry practitioners and the security community at large.
Hacking techniques represent ways and means by which computer programs can be made to behave in ways they should not. These techniques go beyond the technology realm and can be used to test security policies and procedures. Hacking technologies are used to refer to the tools and automated programs that can be used by perpetrators against an organization to cause critical damage. As technology advances, the skills required to execute a hack are much less, as pre-compiled programs are available to wreak havoc with simple point-and-click.
Isn't this knowledge harmful? Why is it so easily accessible to the public?
EC-Council fulfills its social responsibility by ensuring that only people with at least two years of security experience are eligible for the program. In addition, all candidates are required to sign an agreement in which they undertake to respect the knowledge acquired and not to misuse it in any way. The participant also undertakes to comply with all laws of their respective country of residence when using the acquired knowledge. In addition, the CEH exam is difficult to pass as participants must have in-depth knowledge in order to obtain the globally recognized ethical hacking certification.
CEH (MASTER)
To earn the CEH Master designation, you must successfully demonstrate your knowledge of ethical hacking by passing two distinctly different tests. First, you must attempt to successfully pass the ANSI Accredited Certified Ethical Hacker (CEH) multiple-choice exam. Once you have completed this first step, you can move on to the second part of earning the CEH master's designation, the CEH practice exam.
The goal of this course is to help you master ethical hacking methods that can be used in a penetration test or in an ethical hacking situation.
Who is the EC-Council Certification CEH suitable for?
Tectrain.ch's EC-Council Certified Ethical Hacker training course will greatly benefit security officers, auditors, security professionals, site administrators and anyone concerned about the integrity of network infrastructure.
Mobile ethical hacking
Again, this course is ideal for students who are ready to learn mobile device and mobile app penetration testing and ethical hacking - whether you're a professional developer or just a beginner.
What you will learn:
- Learn more about mobile cybersecurity for mobile apps and devices
- Learn more about mobile applications and penetration testing for games
- Learn more about Android and iOS fundamentals
- Learn more about Java & Swift Fundamentals
- Learn more about ethical hacking fundamentals
6. EC-Council Certified Penetration Testing Professional (C|PENT)
The CPENT series consists of entire network segments that simulate an enterprise network - this is not a computer game simulation, but an accurate representation of an enterprise network that provides the tester with the latest challenges. One benefit of hands-on learning in a live cyber environment is that candidates encounter multiple layers of network segmentation. EC-Council's CPENT course teaches participants how to navigate through these layers so that if one segment is accessed, they know the pivoting techniques required to reach the next.

CPENT candidates are for example:
- Ethical hackers
- Penetration testers
- Network server administrators
- Firewall administrators
- Security testers
- System administrators and risk assessment experts
Licensed Penetration Tester - LPT (Master)
This exam has only one purpose: to distinguish the experts from the novices in penetration testing!
To earn the LPT (Master), participants must score at least 90% on a 24-hour exam. The exam requires that they have mastered the deployment of advanced pen testing techniques and tools including multi-stage pivoting, operating system vulnerability exploits, SSH tunneling, host-based application exploits and privilege escalation. In addition, web server and web application exploits such as arbitrary local and remote file uploads, SQL injection and parameter manipulation, etc. must be demonstrated - all in a real-world scenario on hardened machines, networks and applications.
Python for pentesters
Python is packed with many reverse engineering and exploitation libraries. It's a great language to learn if you want to familiarize yourself with information security tasks.
This course starts from scratch and equips you with the latest tools and techniques available for Python pentesting. By the end of the course, you will be able to successfully use Python scripts for penetration testing in a variety of systems.
Web app penetration testing
First, you'll learn about scoping and mapping your target application properly. Next, you'll spend some time analyzing and scanning the application's attack surface to trigger potential vulnerabilities in your target, and then dive deep into the results to validate your findings. Finally, you'll conclude by learning how to properly customize and report your findings to your audience.
7. EC-Council Network Defense Essentials (N|DE)
Network Defense Essentials is an introductory cybersecurity course that covers the fundamental concepts of information security and network defense. Those interested in a career in information security will learn the various fundamentals of information security and network defense and what to expect in the field of network defense.
The course provides you with a holistic overview of the key components of information security such as identification, authentication and authorization, virtualization and cloud computing, wireless network, mobile device and IoT device and data security. This active learning course ensures that participants gain practical experience and skills required for a future in cyber security.
Ethical Hacking Essentials (EHE)
Ethical Hacking Essentials is an introductory cybersecurity course that prepares students to begin their career in cybersecurity by learning ethical hacking and penetration testing fundamentals. This course introduces students to cybersecurity threats, vulnerabilities and attack vectors such as web application, wireless, mobile IoT, network level attacks and countermeasures. Students will gain hands-on experience and skills needed for a future in cybersecurity.
Digital Forensics Essentials (DFE)
The EC-Council certification, Digital Forensics Essentials is the ideal entry point for anyone interested in understanding digital forensics.
This course introduces students to the fundamentals of computer forensics as well as the computer forensics investigation process. Be prepared to learn about the dark web, Windows, Linux, malware forensics and much more!
8. EC-Council Certified Encryption Specialist (E|CES)
The EC-Council Certification Encryption Specialist (ECES) introduces professionals and participants to the field of cryptography. Participants will learn the basics of modern symmetric and key cryptography, including the details of algorithms such as Feistel Networks, DES and AES. Anyone involved in the selection and implementation of VPNs or digital certificates should attend this course. Once you have successfully completed this course, you will be able to select the encryption standard that is most beneficial to your organization and understand how this technology can be used effectively.
9. EC-Council Certified Blockchain Professional (C|BP)
The EC-Council Certified Blockchain Professional (CBP) certification is designed to help professionals gain the knowledge they need in blockchain technology to understand its impact on business and beyond. The Certified Blockchain Professional course starts with the technical fundamentals of blockchain such as distributed and decentralized systems, cryptography and mining.
Participants will learn how to develop applications using Ethereum. In addition, participants will explore various blockchain enterprise applications such as Hyperledger, pioneered by the Linux Foundation and widely used by IBM. Most importantly, the course covers multiple blockchain implementation concepts by immersing participants in sustainable and scalable blockchain development - the cornerstone of a decentralization strategy.
Is a blockchain certification from EC-Council worth it?
Blockchain developers are and will be in high demand over the next 5-10 years and the technology has the potential to change the way businesses operate forever.
What are the eligibility requirements for CBP?
The EC-Council CBP certification is tailored for full-stack developers. To get more out of this course and apply the concepts introduced there, you need to know the following:
- Object-oriented programming
- Working with asynchronous JavaScript code
- Developing the front-end and back-end of a web application with JavaScript
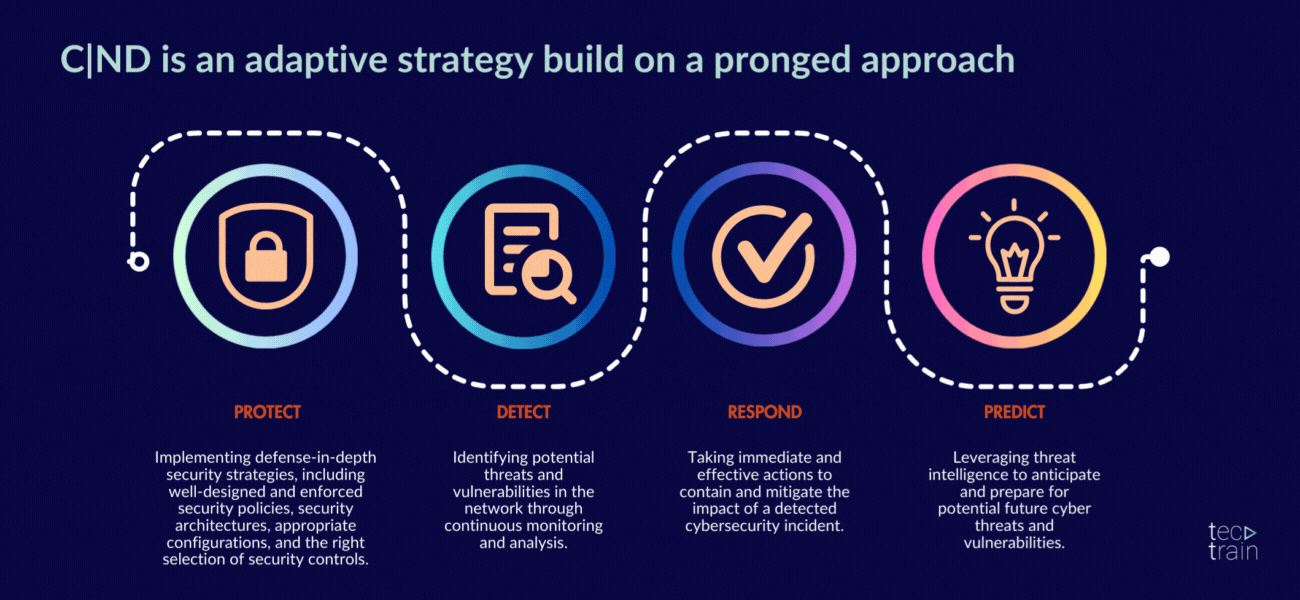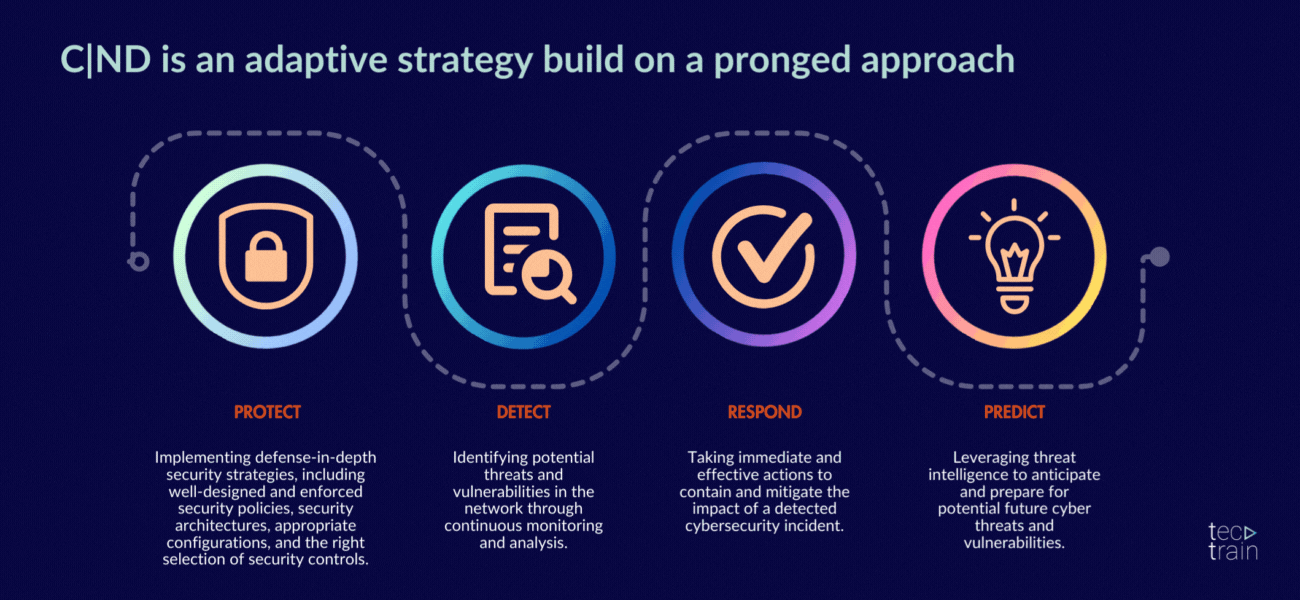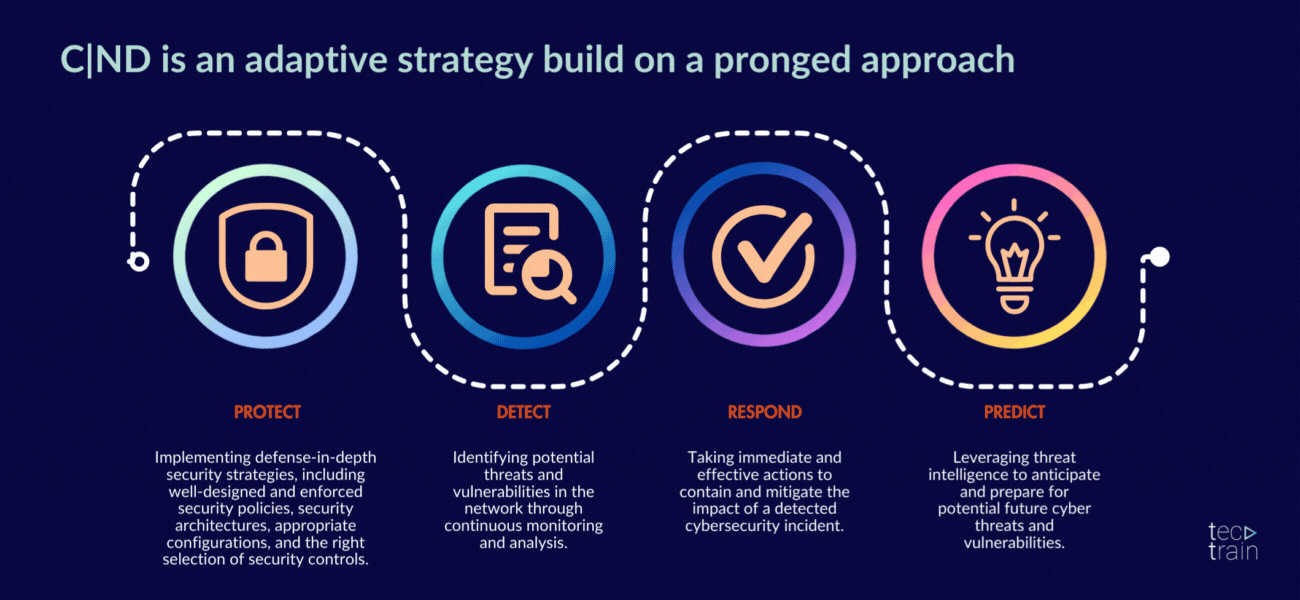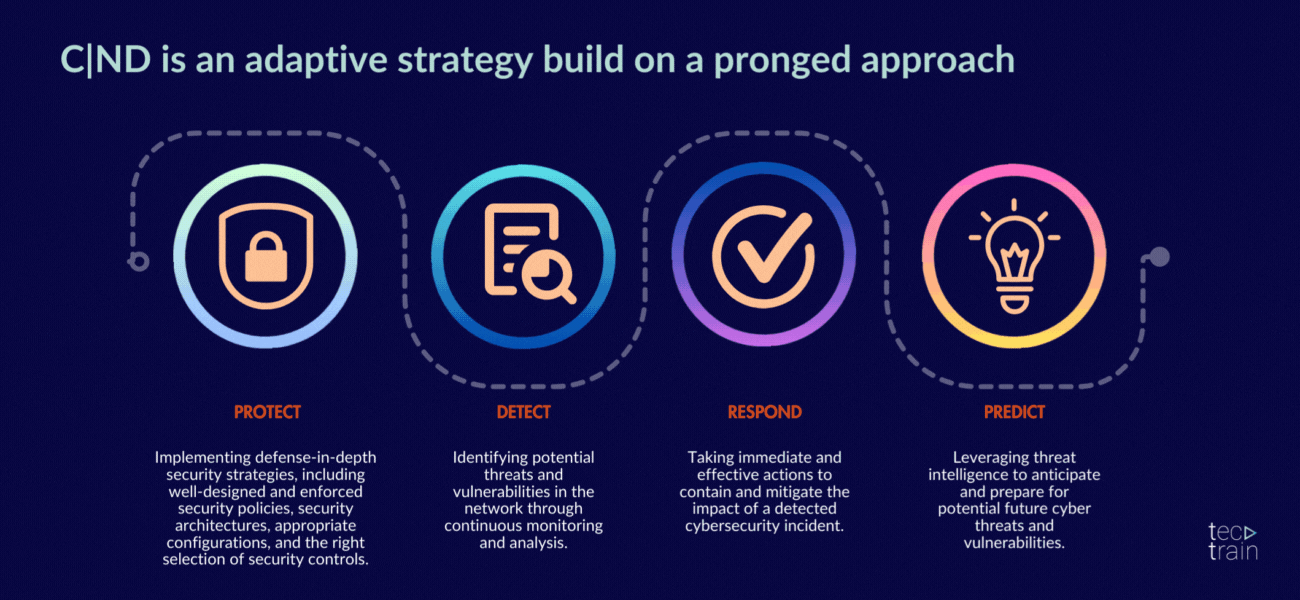
10. EC-Council Certified Network Defender (C|ND)
The program prepares network administrators to identify which parts of an organization need to be scanned and tested for security vulnerabilities, and how to reduce, prevent and mitigate risks on the network. CND covers the protection, detection, response and prediction approach to network security.
ICS/SCADA Cybersecurity
The ICS/SCADA Cybersecurity course is a practical training module that teaches the basics of security and protects network architectures from attacks.
Who is the EC-Council ICS/SCAFDA certification suitable for?
This course is specifically designed for IT professionals who are involved in the administration or management of their organization's IT infrastructure and are responsible for establishing and maintaining information security policies, practices and procedures. The focus of the course is on Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems.
Identity and Access Management
Includes basic concepts, as well as the technologies and different approaches to implementing effective IAM in the enterprise, web services and government.
Linux basics
If you understand Linux, you will also understand the operating system that powers much of the internet. This beginner's course will make you Linux literate, even if you don't know anything about this operating system yet.
11. EC-Council Certified Secure Computer User (C|SCU)
Soar to new heights with this introduction to cybersecurity! The purpose of the CSCU training program is to provide participants with the necessary knowledge and skills to protect their information assets. This course will immerse students in an interactive environment where they will gain a basic understanding of various computer and network security threats such as identity theft, credit card fraud, online banking phishing scams, viruses and backdoors, email hoaxes, online lurking sex offenders, loss of confidential information, hacking attacks and social engineering. More importantly, the skills learned from the class will help you take the necessary steps to mitigate security risks.
12. EC-Council Certified Security Specialist (E|CSS)
The EC-Council Certified Security Specialist (ECSS) certification enables participants to improve their skills in three different areas, namely information security, network security and computer forensics. Information security plays a crucial role in most organizations. It is necessary wherever information, information processing and communication must be protected from the confidentiality, integrity and availability of information and information processing.
In communication, information security also includes the trusted authentication of messages, which additionally includes the identification of the verification and recording of the approval and authorization of information, the non-alteration of data and the non-repudiation of communication or stored data.
13. EC-Council Certified Cloud Security Engineer (C|CSE)
Cloud technology has changed the technology landscape and will continue to do so in the coming years. EC-Council's Certified Cloud Security Engineer (CCSE) is a vendor-neutral course that focuses on cloud security practices, technologies, frameworks and principles to deliver a balanced mix of theoretical and practical skills you need to become a cloud security expert.
Who should attend this course?
- Network security engineers
- Cybersecurity Analysts
- Network security analysts
- Cloud administrators and engineers
- Network security administrators
- Cloud analysts
- Cybersecurity engineers
- People working in network and cloud management and operations
14. EC-Council Certified Incident Handler (E|CIH)
The EC-Council Certified Incident Handler (ECIH) certification focuses on a structured approach to the Incident Handling and Response (IH&R) process. The IH&R process includes phases such as incident handling and response preparation, incident validation and prioritization, incident escalation and notification, forensic evidence collection and analysis, incident containment, system recovery, and incident remediation. This systematic handling and response process creates awareness among incident responders to know how to respond to different types of security incidents.
15. EC-Council Certified SOC Analyst (C|SA)
The Certified SOC Analyst (CSA) program is the first step to joining a Security Operations Center (SOC). It is designed for current and aspiring Tier I and Tier II SOC analysts to gain proficiency in conducting entry-level and intermediate operations.
CSA is a training and skills development program that helps participants gain trendy and in-demand technical skills through instruction from some of the most experienced trainers in the industry. The program focuses on creating new career opportunities through extensive, meticulous knowledge with enhanced level skills to dynamically contribute to a SOC team. Being an intensive 3-day program, it thoroughly covers the fundamentals of SOC operations before imparting the knowledge of log management and correlation, SIEM deployment, advanced incident detection and incident response. In addition, the candidate will learn to manage various SOC processes and collaborate with CSIRT when required.
16. EC-Council Certified Threat Intelligence Analyst (C|TIA)
Certified Threat Intelligence Analyst (CTIA) was developed in collaboration with cybersecurity and threat intelligence professionals around the world to help organizations identify and mitigate business risks by converting unknown internal and external threats into known threats. It is a comprehensive, specialist-level program that provides a structured approach to building effective threat intelligence.
In the ever-changing threat landscape, CTIA is an essential program for anyone dealing with cyber threats on a daily basis. Organizations today demand a professional cybersecurity threat intelligence analyst who can extract intelligence from data by implementing various advanced strategies. Such professional programs can only be achieved if the core of the curricula conforms to government and industry published threat intelligence frameworks.
FAQ
How much do you earn as an ethical hacker in the UK?
As an ethical hacker, you can expect an average annual salary of around £47,000 However, your actual salary may vary depending on your experience, expertise and location.
What does an ethical hacker do?
An ethical hacker is an IT security expert who makes authorized attempts to penetrate an organization's networks or systems. The aim is to identify possible security gaps and make recommendations for improving security.
What is a pentest?
A pentest, or penetration test, is a method that ethical hackers use to carry out planned attacks on a company's security infrastructure. This helps to discover potential vulnerabilities that can then be fixed.
How can I obtain an EC-Council certificate?
Tectrain offers you a wide range of training courses and certifications. Here you can register directly for your EC-Council certificate and prove your skills as an ethical hacker or expand your knowledge as a cyber security expert.
Conclusion
The EC-Council Training is a training series that specializes in the areas of information security and ethical hacking. It is designed to provide IT professionals with the skills needed to protect networks, systems and applications from attacks. There are various certifications, including CEH (Certified Ethical Hacker), CHFI (Computer Hacking Forensics Investigator) and CCISO (Certified Chief Information Security Officer).
The CCISO certification consists of five domains: Governance, Risk Management and Compliance, Asset Security, Security Engineering, Communications and Network Security, and Security Operations. The certification is valid for a period of three years and can be renewed. Becoming a Certified Application Security Engineer (CASE) can help improve application security and prevent attacks. It is a valuable certification for anyone working in application development and looking for a career in information security.